If You Wouldn’t Post It on Social Media, Don’t Paste It Into AI

If You Wouldn’t Post It on Social Media, Don’t Paste It Into AI | it.ie AI Data Privacy & Security If You Wouldn’t Post It on Social Media, Don’t Paste It Into AI JG John Grennan • 12/02/2026 AI tools like ChatGPT, Gemini and others have quickly become the modern office assistant. They summarise emails, […]
Domain Registration Scam Warning

Domain Registration Scam Warning 2026 | Fake Renewal Invoices Author: John Grennan | Published: January 22, 2026 Security Alert Domain Registration Scam Warning. Fake Renewal Invoices Are Back Domain registration scams are not new. But they are getting more polished, more convincing, and more likely to catch busy businesses off guard. We were recently sent […]
The 2025 Christmas Naughty List
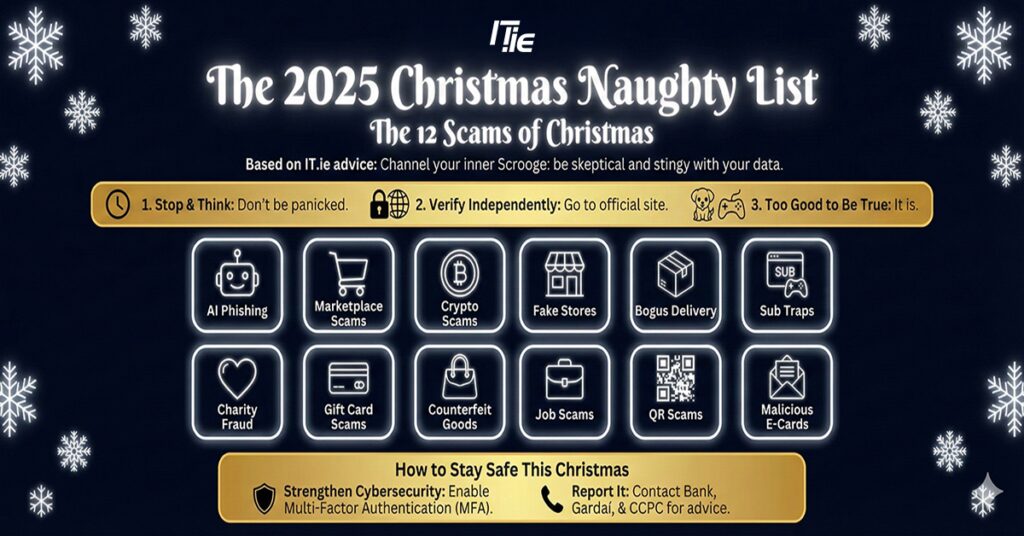
Managed IT Services IT Support Louth Welcome to IT.ie. The home of Managed IT Services in Co Louth and nationwide. We specialise in providing Managed
Cyber Security Myths vs Reality: What Irish SMEs Need to Know
Cyber Security Myths vs Reality: What Irish SMEs Need to Know Our news feeds are constantly scrolling with stories of major brands falling victim to cyber-attacks. It is easy to look at those headlines and think, “Well, at least I’m not them.” However, that mindset is dangerous. Many Irish businesses are operating under a set […]
The Privacy Paradox with AI
Artificial intelligence (AI) is rapidly transforming how we work, communicate, and make decisions but concerns around data privacy have never been more pressing. The rapid rise of AI assistants such as Microsoft Copilot, OpenAI’s ChatGPT, and Google Gemini has brought powerful capabilities to our fingertips but at what cost to our personal and organisational data? […]
Press Release: 30% of office workers have tried to gain unauthorised access to a colleague’s device in the last year

Research from IT.ie and SonicWall also found that 35% have actively sought out private information about a colleague, client, or customer from a work computer system 38% have engaged with a scammer either intentionally or unintentionally One in four have sent an angry response to someone they presumed to be a scammer 17% say they […]
EU Cybersecurity Regulations: What You Need to Know in 2025

John Grennan, Eamon Gallagher & Wayne Morgan June 24, 2025 In light of the ever-evolving cyber threat landscape, the European Union is stepping up efforts to protect EU citizens data. From data protection and incident response to operational resilience, a wave of cybersecurity legislation is reshaping how organisations across the EU must operate. In this […]
Press Release: One in 10 admit to pirating content on their work devices

Dublin, 27th May 2025: IT.ie, a leading Irish IT managed services company, is today urging SMEs to strengthen their cybersecurity defences as the deadline for the EU’s NIS2 directive approaches. The need for businesses to reinforce their cybersecurity measures is highlighted in research carried out by IT.ie and SonicWall, which found that one in 10 […]
Break Free from Digital Debt: Reclaim Control with CyberProtect

The digital world is always on, and while we’re more connected than ever, are we actually more productive? For many businesses, the answer is a resounding no. Digital tools were designed to make our lives easier, but somewhere along the way, the tech stack became bloated, fragmented, and overwhelming. In his book Sapiens: A Brief […]
The Drive to 75: Finding the Perfect Balance in Microsoft Secure Score

Cyber threats are evolving at an alarming rate, and businesses of all sizes are in the crosshairs. Measuring your organisation’s security readiness isn’t just a useful metric – it’s an imperative. But how can you do that? This is where Microsoft Secure Score comes in—a powerful benchmark that evaluates your security posture within Microsoft 365. […]

