Stop attackers in their tracks with our managed cybersecurity detection and response solution backed by a world-class security operations center.

Windows & macOS event log monitoring, advanced breach detection, malicious files and processes, threat hunting, intrusion detection, 3rd party NGAV integrations and more.
Firewall and edge device log monitoring integrated with real-time threat reputation, DNS information and malicious connection alerting.

Secure the cloud with Microsoft 365 security event log monitoring, Azure AD monitoring, Microsoft 365 malicious logins and overall Secure Score.

Managed SOC as a Service (security operation center) is a managed service that leverages our Threat Monitoring Platform to detect malicious and suspicious activity across three critical attack vectors: Endpoint | Network | Cloud. An elite team of security veterans hunt, triage and work with your team when actionable threats are discovered including:
The most comprehensive set of features means you can focus you’re your business while our team of security experts ensures that you have the most advanced protection leveraging your existing tools and technologies across endpoint, network and cloud.
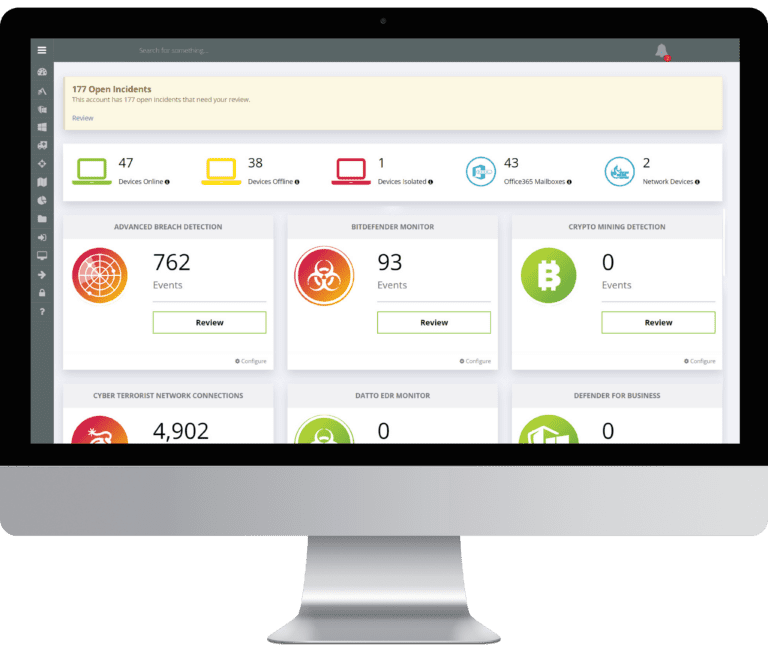
Monitor, search, alert and report on the 3 attack pillars: network, cloud and endpoint log data spanning Windows and macOS, Firewalls and Network Devices, Microsoft 365 & Azure AD without requiring SIEM hardware.
Real-time threat intelligence monitoring, connecting to premium intel feed partners giving our customers the largest global repository of threat indicators for our SOC analysts to hunt down attackers.
Detect adversaries that evade traditional cyber defenses such as Firewalls and AV. Identifies attacker TTPs and aligns with Mitre Attack, producing a forensic timeline of chronological events to deter the intruder before a breach occurs.
Real-time monitoring of malicious and suspicious activity, identifying indicators such as connections to terrorist nations, unauthorized TCP/UDP services, backdoor connections to C2 servers, lateral movements and privilege escalation.
Use your own malware prevention or leverage our command and control app for Microsoft Defender backed up with a secondary line of defense using our malicious detection of files, tools, processes and more.
Our SOC analysts investigate each alert, triage the data and produce a ticket to your PSA system accompanied with the remedy details so you can focus on your operations without hiring security additional engineers.
If you would like to talk to us or just have a question about any of our services, please don’t hesitate to contact us and we’ll get right back to you.
We and our partners use cookies and process personal data (like unique IDs and Browse behaviour) to improve your experience, personalize content and ads, measure performance, and understand our audience.
You have the right to choose which cookies you'd like to enable. By clicking "Accept", you consent to all cookies. You can also "Reject" non-essential cookies, or manage your preferences through "View Preferences" below.
For more information on how we use cookies and your data, please read our Cookie Policy and Privacy Policy.
Fill in your details below and hit download.