Automated Pen Testing As-a-Service (PTaaS)
Penetration Testing
Penetration testing, also referred to as pen testing is a standard approach to quantifying and identifying such vulnerabilities across an organisation. The test will usually try to simulate a real-life threat and demonstrate how a system would hold up against such a threat.
By assessing if an IT System is susceptible to a cyber-attack, you will be able to plan, repair and strengthen your organisation’s infrastructure defences against such attack.
An internal pen test is undertaken within an organisation’s network, searching for vulnerabilities from within. An external pen test is performed remotely, with an ethical hacker looking for security vulnerabilities in internet-facing assets such as FTP and mail servers.
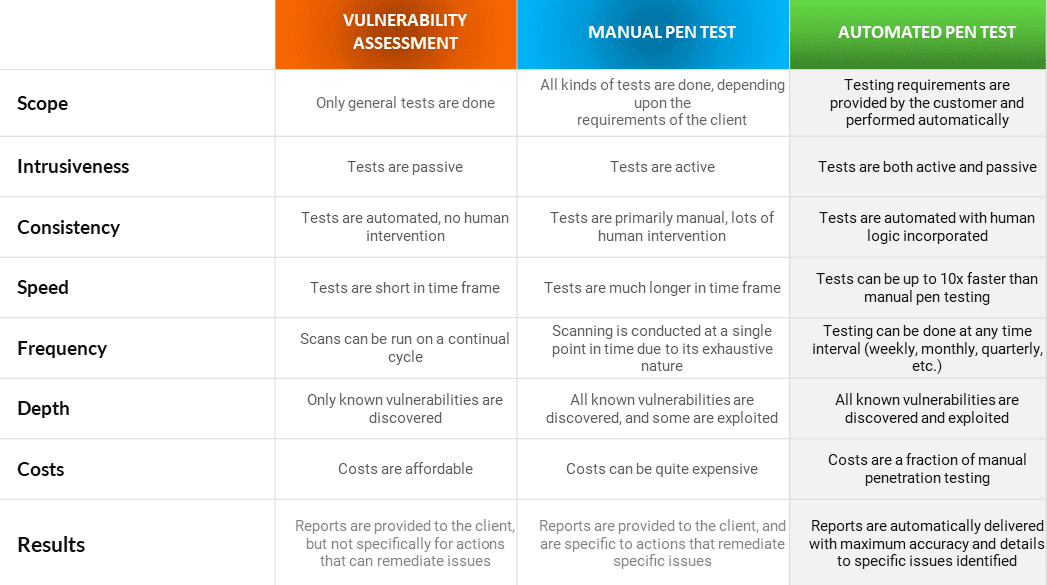
IT.ie are proud to partner with Kayseya to deliver a revolutionary solution that allows you to have a full-blown penetration test every month, instead of just once a year.