3.2 Billion Email Credentials Leaked Online – How Do You Protect Your Credentials?
Earlier this month it was revealed that hackers now have access to over 3 billion emails and passwords. This is being called the largest data breach of all time and actually consists of a combination of smaller data breaches that have occurred over the past several years. Named the Compilation of All Breaches, or COMB and odds are that your email and password are included.
To test this I checked both my private Gmail account and my business IT.ie account using the free tool, Have I Been Pawned. What I found was that my private Gmail address had been compromised in several breaches, however, luckily my business Outlook account has not been compromised. Pawned is a great tool and lists any data breach where your credentials were compromised.
In this post, I will look at some of the ways you can mitigate against a data breach of your credentials.
Use the Underpants Rule
The underpants rule is straightforward and involves only 3 easy to follow steps that are good practice for both password protection and underwear, in general. So, treat your passwords like your underpants.
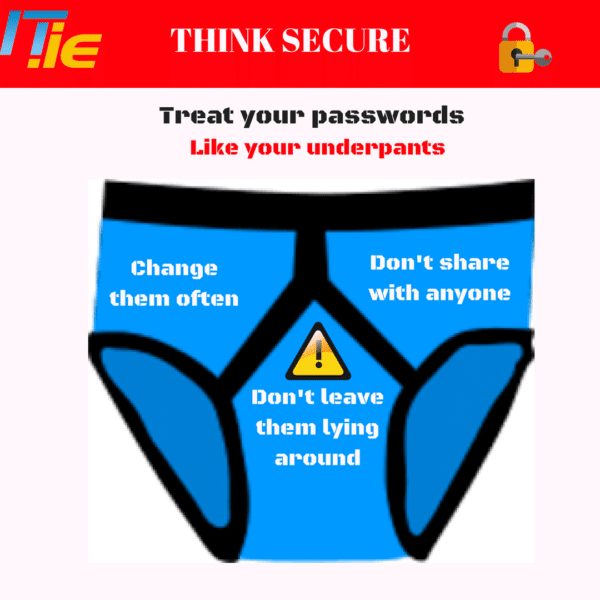
Change them often – Set a policy in place whereby passwords must be changed every 30, 60 or 90 days. By doing this you are not preventing a compromise but given that most people won’t know for months or even years that their credentials have been compromised, it narrows the window whereby the compromise could be of harm to you or your organisation.
Don’t share them with anyone – It isn’t always good to share and just as you shouldn’t share your underwear, never share your passwords.
Don’t leave them lying around – Don’t write your password on a post-it note and leave it stuck to your screen or under your keyboard.
Creating Strong Passwords
You might think “Dave1” or “Siobhan29” is a secure password. It’s not. Contrary to popular opinion, adding special characters like *%%EDITORCONTENT%%amp;@!_ alone will not help you very much either.
Here are some essential tips for creating a strong, unguessable password:
- Include letters (lower and upper case), numbers, and symbols. Turn Dave1 into @G1tr3gr8st_!@#$ instead.
- Make it 12 characters, minimum.
- STOP USING YOUR LOVED ONES OR PET’S NAMES.
Use a Password Manager
Creating complex passwords, as shown above, do create their own problems for you as you can’t easily remember them and makes it more likely that you’ll note them somewhere that itself can be seen or compromised. A password manager is a great tool that allows you to both create and store your complex passwords safely and securely. I’ve been using LastPass via the Chrome extension (also works with Edge) for a few years now and honestly don’t know how I could work efficiently without it. Plans start from free, and all your logins are stored in the tools vault. When signing up to new online accounts it both suggests and stores your complex passwords and allows for seamless logins to the various sites you are connected to too. There are plenty of good password managers available for free so do a bit of research and pick one that works for you.
Protect your Devices
Whether it’s your laptop, desktop, phone or any device that has your login credentials, NEVER LEAVE IT UNSECURED. Did you know that all you have to do on an open device is open chrome://settings/passwords in the address bar and your login credential are there for the world to see? Most devices now have a mix of PIN and biometric security locks to allow access, so make sure that at least one is enabled and ensure that your device locks after a maximum of 5 minutes of inactivity.
While I hate to say it, hackers are pretty clever and are always coming up with new ways to compromise your data. On top of that many hacks and data breaches are state-sponsored. There is no sure-fire 100% guarantee against a hack or credentials compromise, but by employing a robust password policy, utilising a password manager and a bit of common sense, you can greatly mitigate against a compromise.
IT.ie provide a host of cybersecurity solutions to help you protect your valuable data and IT systems, including AI-powered Managed Email Security that greatly reduces spam and phishing attacks. If you fall victim to a serious data breach or accidental loss or destruction of data, a reliable data backup and disaster recovery solution can get you back in business and fully operational with the minimum of disruption. Email is still the number one threat vector and no matter what solutions you employ; common good sense and good practices are your best defence.



