It has come to our attention via CSIRT-IE that there is current wave on Ransomware attacks taking place and urge everyone to be vigilant when in receipt of unsolicited emails. If you are unsure or suspicious as to the content of an email make sure you contact your IT department or IT Support Company. Opening unsolicited emails may result in a ransomware attack that will, at the very least, cost a large sum of money to retrieve encrypted file.
This particular wave of attacks concerns the receipt of a Word Doc that requires a password to open. It appears that a simple password of 1234 is provided, however don’t trust any variant of this. The Word document contains a malicious macro that downloads AZORult malware. The AZORult malware reaches out from the compromised host and downloads the Hermes ransomware. The following screenshots depict the infection process.
Malware Deletes Certain File Types
The malware then runs a file called window.bat which attempts to delete the following file types if they exist on the infected system, .VHD, .bac, .bak, .wbcat, .bkf, .set, .win and .dsk. In addition, any file names containing Backup or backup are deleted and it attempts to delete shadow copies.
It attempts to delete these files from the c:, d:, e:, f:, g: & h: drives. This gives the cybercriminal control of your device and prevents you from accessing your valuable data.
Backup, Backup, Backup
The only surefire way to protect your data from a cyber attack is the employ the services of a trusted backup service provider. In the event of disaster, you really need to think about disaster recovery. In partnership with Datastring we provide DRaaS (Data Recovery as a Service) to many clients. If you would like to talk about online backup or disaster recovery, just give us a call and we’ll be happy to explain how we can design, configure and manage every aspect of your cloud backup or disaster recovery solution.
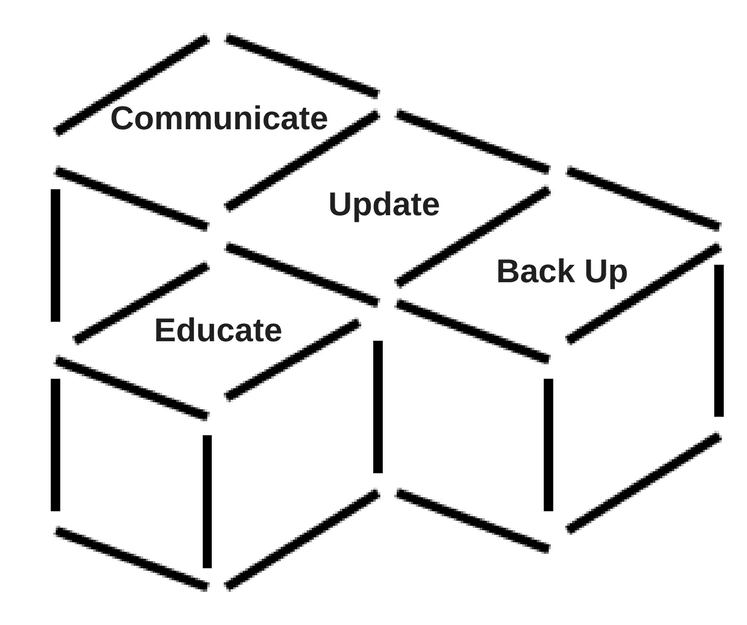
At IT.ie we recommend that you implement C.U.B.E to mitigate the chances of attack and reduce its impact, should you fall victim
- Communicate: with employees to develop a strategy to inform employees if a virus reaches the company network.
- Update: all software, including operating systems, antivirus software and all other applications.
- Back Up: all information every day, including information on employee devices, so you can restore encrypted data if attacked. It is strongly advised that you use an online backup service.
- Educate: staff on cyber security practices, emphasising not to open attachments or links from unknown or untrusted sources.