Ransomware – Do You Trust Your Inbox?
Just this morning (14/05/2021) it was revealed that the Irish Health Service Executive (HSE) has been forced to take their IT Systems offline in response to an ongoing ransomware attack. This post was originally published in April in response to similar attacks on educational institutions in Ireland, however, the steps we recommend here can and should be implemented by all users of IT systems across every sector.
While most of the world is working together to fight the ongoing global pandemic, cybercriminals see this as an opportunity, and we are seeing more and more attacks on the services and institutions vital in this fight. Every business and every private user is a potential target of cybercrime but more and more we are seeing large scale attacks that disrupt healthcare, education, and government services.
Email is the No.1 threat vector and most cyber-attacks including ransomware occur because of an action carried out by the recipient of an email. So, do you trust your inbox?
The following tips are designed to help you investigate an email and avoid falling victim to a ransomware or other cyber-attack.
- Suspicious Sender
Cybercriminals use various spoofing techniques to trick users into believing an email is legitimate. Check the domain closely for close ‘cousin’ domains. Be cautious when reading email on your mobile device, as only the display name may be visible even if the email is bogus.
- Subject Line & Tone
Enticing, urgent, or threatening language is commonly used to encourage the recipient to take immediate action. Evoking a sense of curiosity, greed, or fear is a common tactic among phishing schemes. Something similar is seen in scam phone calls and text messages, known as vishing, whereby the caller may tell you that they are from revenue or the Gardai and that you must pay a sum of money to avoid a serious financial or legal penalty.
- Greetings
Phishers often send out mass emails to gather information, so they use generic greetings. Sophisticated phishers, however, personalise their emails with information such as names, email addresses, and even breached passwords, to make the email seem more legitimate.
- Errors
Read the email carefully. Grammatical errors are an obvious red flag, but sophisticated hackers do not make glaring errors. Instead, there may be more subtle mistakes, such as minor spacing issues or the use of symbols instead of words. In some cases, there will be no errors.
- Links
Avoid clicking links until you are certain that they are safe and that the destination they take you is trusted. An email recipient clicking on dangerous links is the most common entry method to your systems by cybercriminals. Before clicking, hover over the link to see the URL of where the link actually leads, and beware of link shorteners, such as Bitly or TinyURL. Keep in mind that phishing emails can include clean URLs in addition to the phishing URL to trick users and email filters. If in doubt, Don’t Click.
- Attachments
Be wary of emails that include attachments. Phishing emails may include a link in an attachment, rather than the body of the email, to avoid detection by an email filter. Attached bogus Word docs and PDFs are another common entry method for criminals.
- Images
Cybercriminals can easily replicate brand logos, images, and badges in emails and web pages that are indistinguishable from the real thing. Consider all the above factors as you decide whether to click.
As you can see there are steps you can take to determine if an email is legitimate or suspicious, however, it is an action that you take, such as clicking on a link that allows the criminals access to your systems.
We are human and as such we make mistakes, so the best practice is to implement a system to mitigate against an attack. The C.U.B.E system is a very simple 4 step method that will greatly reduce your chances of an attack.
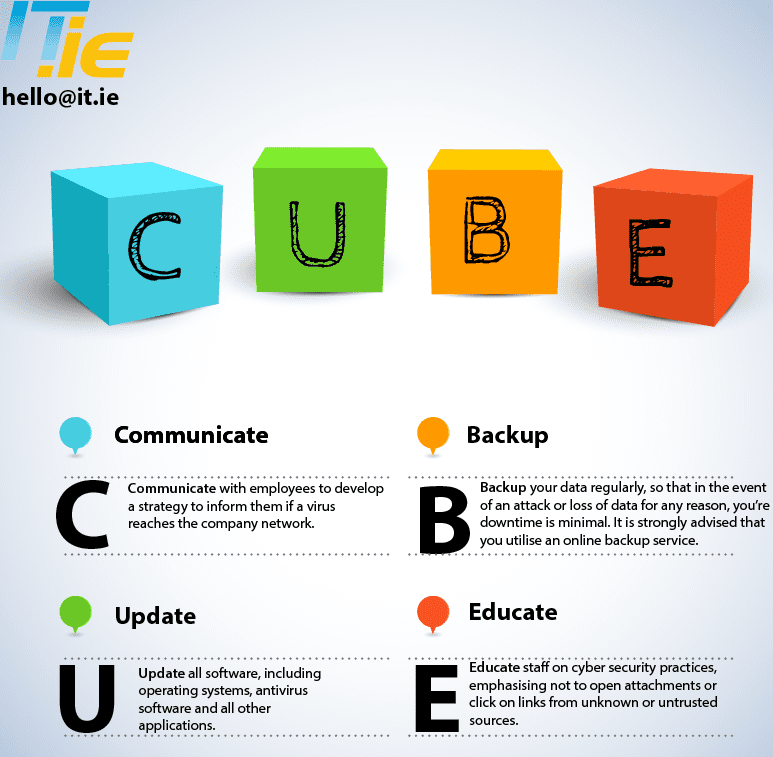
- Communicate: with employees to develop a strategy to inform employees if a virus reaches the company network.
- Update: all software, including operating systems, antivirus software and all other applications.
- Backup: your data regularly so that in the event of an attack or data loss for any reason, your downtime will be minimal. It is strongly advised that you utilise an online backup service.
- Educate: staff on cybersecurity practices, emphasising not to open attachments or click on links from unknown or untrusted sources.
IT.ie are an ISO 27001 and Guaranteed Irish accredited provider of Managed IT Services and IT Security to schools and businesses nationwide. If you would like to know more about us then please visit our website www.it.ie and should you have any concerns about your current IT systems or data protection please call (01) 8424114 or email hello@it.ie and we’ll be happy to help.